This example illustrates an insecure deserialization vulnerability in PHP code, categorized as CWE-502: Deserialization of Untrusted Data.
User.php
| |
The user provides valid login credentials.
login.php
| |
Initially, the user “test” is denied access.
profile.php
| |
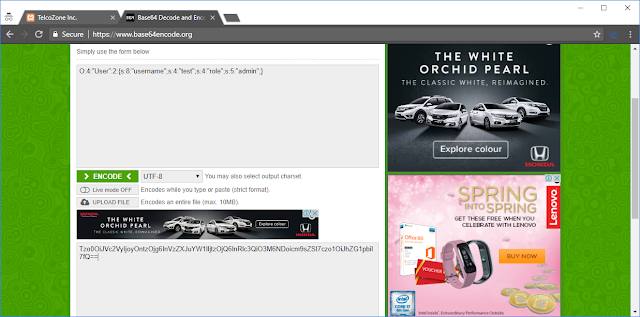
The “data” parameter, containing a base64-encoded serialized PHP object, is captured.
The base64-encoded string is modified to change the user’s role from “user” to “admin”.
The manipulated base64 value is used to gain administrative privileges.
The user is now recognized as an administrator.
Reference:
https://www.owasp.org/index.php/Top_10-2017_A8-Insecure_Deserialization
https://cwe.mitre.org/data/definitions/502.html