Cybersecurity is a rapidly changing field with a significant influence on all areas of business—studies show that there are trillions of dollars](https://www.mckinsey.com/capabilities/risk-and-resilience/our-insights/cybersecurity/new-survey-reveals-2-trillion-dollar-market-opportunity-for-cybersecurity-technology-and-service-providers) on the line. In this informal Q&A, Gökay Pekşen, a Toptal security engineer, responds to inquiries from software developers worldwide, addressing key compliance structures, essential cloud and AWS security assessments, and the significance of [DevSecOps in the cloud.
Early in his career, Gökay earned the distinction of becoming one of Turkey’s pioneering Certified Ethical Hackers; he went on to create Turkey’s first DevSecOps continuous integration and continuous delivery (CI/CD) system. He is the founder and CEO of Prime Threat, a cybersecurity firm specializing in GDPR compliance and risk management, and brings 15 years of IT security experience to this discussion.
Note from the editor: For clarity and brevity, some questions and answers have been modified.
Entering the World of DevOps and Security Engineering
What exactly does a security engineer do? What are some typical tasks you handle daily?
—M.D., Seattle, United States
A security engineer is responsible for protecting an organization’s digital assets and information from cyber threats. Their role involves identifying potential risks, designing and implementing security measures, and enforcing policies and processes to guarantee the confidentiality and integrity of IT systems. Security engineers routinely perform audits, manage system vulnerabilities, and address security breaches, working to preempt security incidents and lessen their effects.
My daily responsibilities change greatly based on the nature of the project I’m involved in. In information security projects, I typically assess the current strategy, examine and modify processes to align with the specific company’s requirements, and generate relevant documentation. When engaged in cybersecurity projects, my focus shifts towards conducting penetration testing, overseeing security rules and configurations, and implementing or improving existing safeguards. I find fulfillment in working with companies as a Virtual Chief Information Security Officer (vCISO) because I enjoy devising strategies and guiding teams on their effective execution.
Could you elaborate on the process of becoming a security engineer? What path led you to this career?
—S.S., Minneapolis, United States
During my undergraduate studies in computer engineering, I achieved the distinction of being among the first Certified Ethical Hackers in Turkey. This accomplishment naturally steered me toward a career in security. Throughout my professional journey, I have consistently prioritized fundamental skills, particularly in Linux, networking, and C. Furthermore, I have dedicated time to training and mentoring others, which has not only expanded my professional circle but also enhanced my own abilities over time.
If you aspire to be a security engineer, pursuing higher education in computer science, information technology, or cybersecurity is advisable. It’s also beneficial to seek internships in these areas. Developing a strong foundation in programming languages, operating systems, and networking principles requires time and dedication. Acquaint yourself with the essential concepts of cybersecurity and DevOps, including encryption, access control, and various security protocols. In addition to technical prowess, strong communication and problem-solving skills are paramount for success in this domain.
For someone with a background in DevOps and cloud infrastructure, what steps would you recommend to broaden their knowledge into cybersecurity and DevSecOps**? Are there any specific books or courses you suggest?**
—W.Y., Vancouver, Canada
As a novice, you could start by pursuing a CEH or OSCP course—but keep in mind that true mastery requires more than certifications alone. Books like Cybersecurity Essentials by Charles J. Brooks and colleagues offer a comprehensive foundation in the fundamental principles of cybersecurity. Individuals with prior experience in DevOps and cloud infrastructure should delve into cloud security, potentially starting with Cloud Security and Privacy by Tim Mather, Subra Kumaraswamy, and Shahid Latif. Subsequently, to further explore integrating security into DevOps, consider reading DevOpsSec by Jim Bird and Securing DevOps by Julien Vehent; both books provide valuable insights into this specific domain.
What exactly is DevSecOps, and what strategies can organizations new to this concept employ to seamlessly integrate security into their DevOps** processes? For those starting from the ground up, what’s the most effective way to cultivate a security-conscious culture?**
—K.S., Montreal, Canada
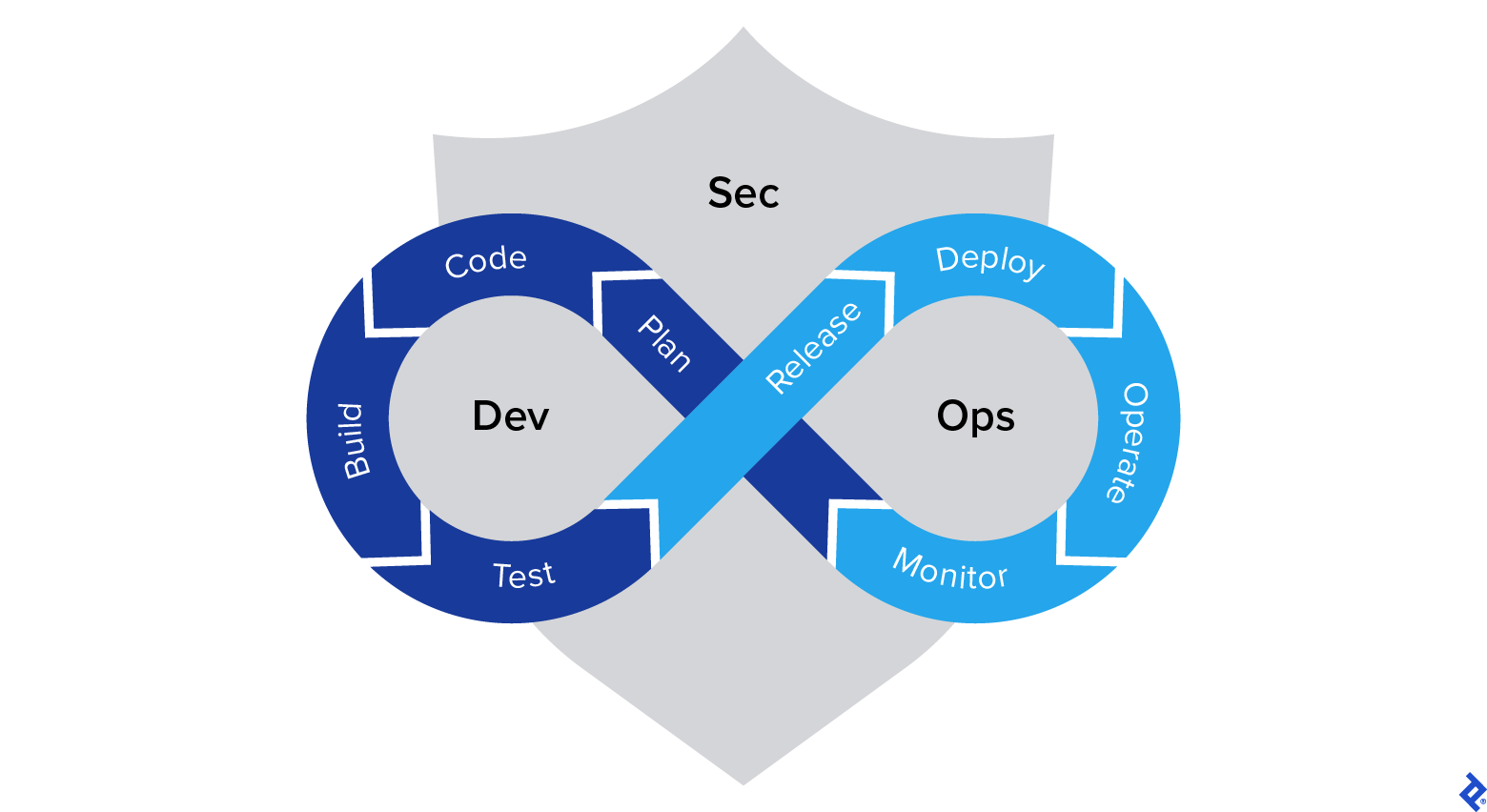
In my view, DevSecOps represents the most crucial transformation a business can currently undertake. Automation serves as a guardian: it removes the potential for human errors and operates without being hampered by the less desirable aspects of human nature. Routine tasks can become tedious, and manual procedures inherently increase the likelihood of mistakes or negligence. The repetitive nature of such tasks can reduce our efficiency, causing us to lose interest and focus. Humans thrive on challenges and novel experiences. Who genuinely enjoys deploying identical virtual machines from a template, implementing the same rules repeatedly, or endlessly scrutinizing source code? I highly doubt anyone does.
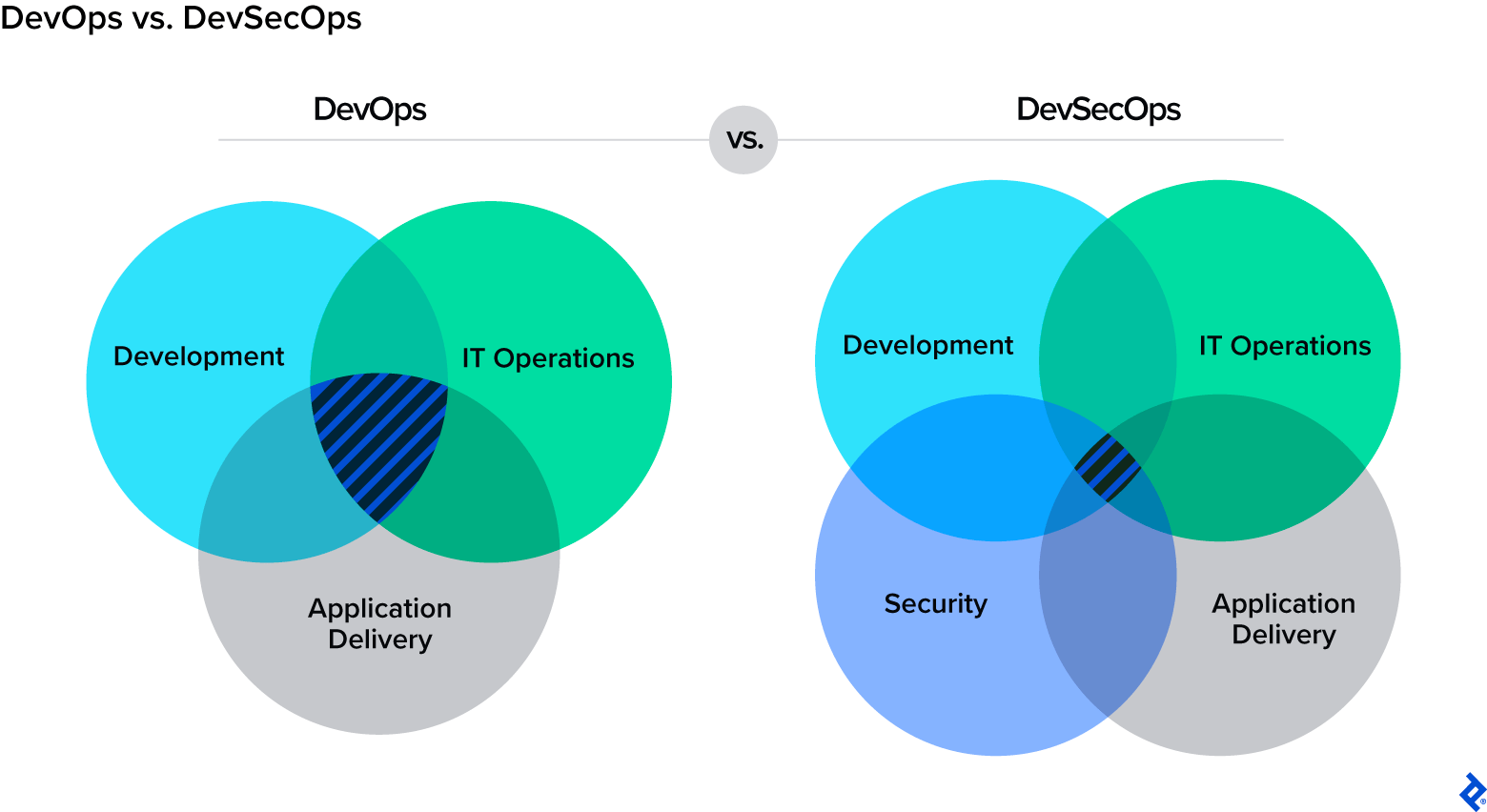
DevSecOps seamlessly combines three vital elements of IT: development, security, and IT operations. While integrating these significant aspects is a challenge in itself, managing them as a cohesive whole poses an even greater difficulty. I have personally implemented and been involved with various CI/CD pipelines, witnessing firsthand the immediate surge in efficiency that comes from eliminating the burden of manual operations.
Establishing a security-first culture is a challenging endeavor; some might even argue that it’s nearly impossible to cultivate solely from within. Resistance from employees accustomed to existing practices is inevitable, and external guidance is often required to navigate this journey. In many cases, this entails enlisting the expertise of a consulting firm.
Essential Security Considerations and Strategies for Businesses
What are the key distinctions between major compliance frameworks? Are there any frameworks particularly well-suited for certain industries?
—K.S., Montreal, Canada
The application of frameworks and standards to specific entities or assets remains consistent, but their implementation varies across industries. Consider this analogy: a firewall functions as a firewall regardless of its location. When you analyze entities based on their characteristics, their behavior within any framework remains consistent. However, the intended purpose of these entities or assets changes depending on the industry. For instance, a web server might handle sensitive financial data for a banking institution but manage personally identifiable information (PII) for a healthcare provider: same fundamental entity, different sector, different implications.
ISO 27001 is widely regarded as the gold standard for security. A significant portion of existing standards and frameworks are based on ISO 27001, making it an ideal starting point for any industry. Applying it to your everyday tasks is the most effective way to understand its intricacies.
What are some fundamental security checks you’d advise for evaluating a web application?
—K.G., Łódź, Poland
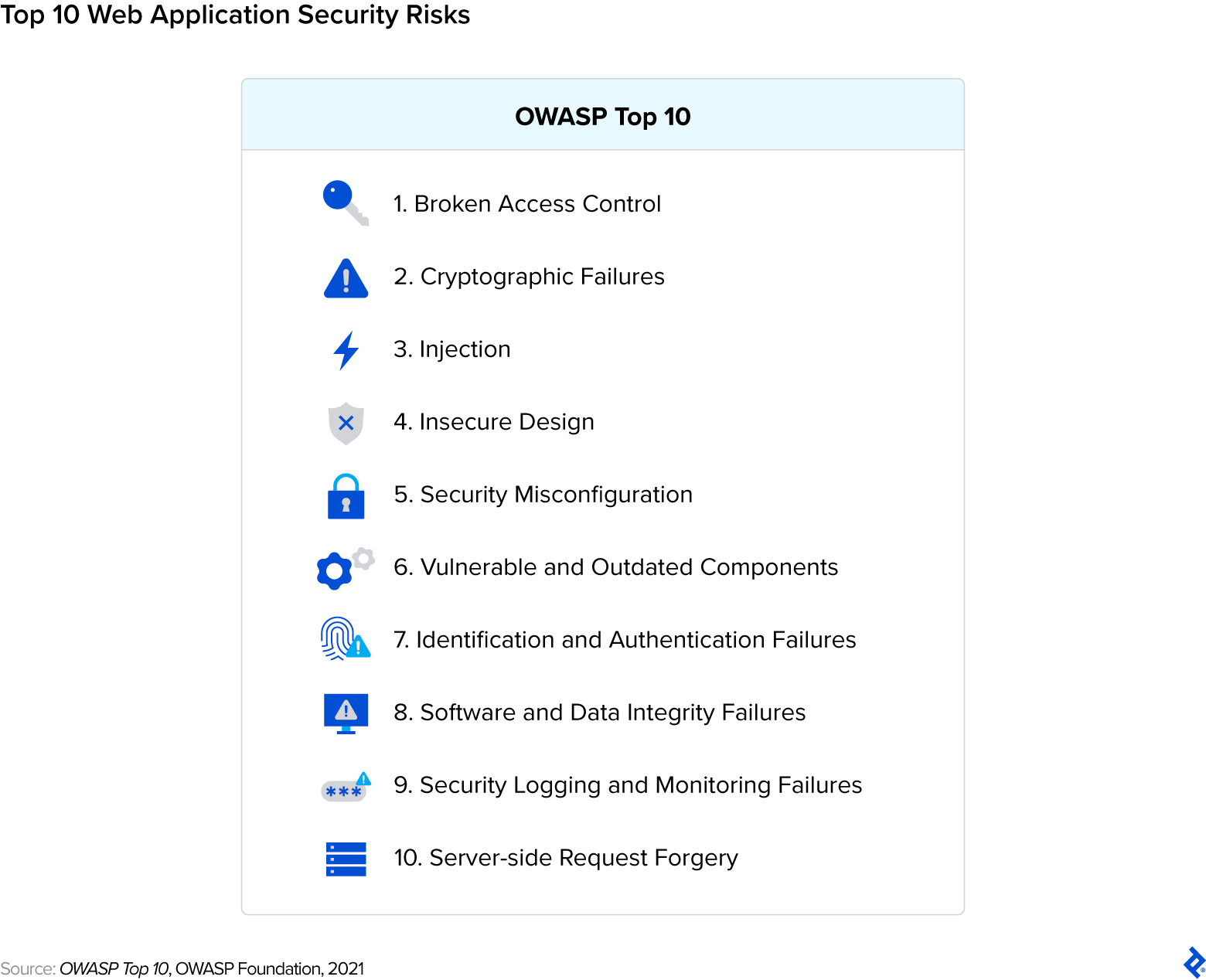
The top 10 list provided by the Open Web Application Security Project (OWASP) is essential for web application security; I strongly recommend it to everyone. It’s a compilation of standardized and developer-friendly resources designed to assist organizations in identifying, ranking, and mitigating the most critical security flaws in web applications. Importantly, it’s regularly updated to reflect the evolving threat landscape.
Given the extensive range of AWS offerings, where should teams begin when it comes to AWS security best practices? What are the most critical services to prioritize securing?
—K.S., Montreal, Canada
The answer hinges significantly on the specific services your organization utilizes. AWS is an expansive platform, offering a wide array of tools and services spanning every layer of the technology stack. Key starting points include Identity and Access Management (IAM), Web Application Firewall (WAF), Virtual Private Cloud (VPC), CloudTrail, S3 bucket security, and Infrastructure as Code (IaC) tools. These are generally applicable to most AWS users operating at scale. Depending on your use case, you might explore additional tools for data security and automation. Consulting with an AWS specialist can be invaluable in determining your precise requirements.
The Future of Cybersecurity
Could you shed light on how advancements in generative AI have influenced your work?
—J.B., Vienna, Austria
I act as the architect, while generative AI takes on the role of the builder. I instruct it to create bespoke documentation sets tailored to meet the specific framework requirements of different companies. I leverage its capabilities to analyze code for potential vulnerabilities or to assess whether a configuration file might make a system susceptible to a cyberattack.
Generative AI feels like a revolutionary advancement in our field, and it’s become an indispensable part of my daily routine. Its ability to quickly provide insights into new tools and technologies is particularly invaluable.
What challenges arise when implementing a zero trust architecture (ZTA) in cloud-based settings?
—O.T., Istanbul, Turkey
Zero trust operationalizes the principle of “never trust, always verify,” contrasting with the more traditional approach of “implicit trust,” where users and devices are assumed trustworthy once authenticated and connected to a permitted network. ZTA centers around meticulous privilege management, aiming to thwart malicious actors from laterally traversing the network and gaining unauthorized access to sensitive data.
However, ZTA is often misunderstood, as security vendors increasingly rebrand existing products to capitalize on the novelty of this term, even when its application might be irrelevant or inappropriate. They often portray firewalls, endpoint protection platforms, or access management tools (like IAM) as functioning like ZTA—which isn’t entirely accurate. Simply deploying a security product on a network differs greatly from cultivating a genuine culture of security within that network; no single product can replace the ongoing efforts required to put ZTA into practice.
Before implementing ZTA, it’s crucial to carefully consider all relevant stakeholders, including shareholders, suppliers, and interconnected relationships. The cloud is intended to be a more flexible and open environment than traditional enterprise software setups. To realize this vision, organizations must meticulously identify what’s genuinely necessary for robust security. Protecting sensitive data isn’t just an ethical imperative; it’s also a sound business strategy. By fortifying your core operations, you cultivate trust and maintain a competitive advantage.
How do you anticipate exploits evolving in the future? We’ve witnessed the rise of binary injections, web exploits, SQL injection, HTTP compromise, and, of course, traditional social engineering techniques like phishing. What lies ahead? What are the latest trends?
—J.O., Fortaleza, Brazil
We’re starting to see generative AI produce entirely new and unprecedented exploits and payloads, effectively turning against us. It won’t be long before we encounter different attack methodologies and exploits as a direct result of the new vectors created by AI. While I’d like to delve deeper into this, revealing too many specifics could be detrimental.
Looking forward, new attacks will adapt and evolve by gathering information from their environment and responding accordingly. We’re also observing attacks targeting AI-based operations, including data poisoning within the generative AI space. The landscape is constantly shifting. Security professionals are already developing prompt firewalls to mitigate the risk of ChatGPT data leakage.
The next significant wave will likely be quantum security, although it might be premature for an extensive discussion. As an interdisciplinary field merging quantum physics, mathematics, and computer science, quantum security opens doors for cross-domain collaboration. Forward-thinking organizations, particularly those prioritizing long-term data protection, are actively exploring and implementing quantum-resistant encryption solutions as a way to future-proof their data security strategies.
However, it’s crucial to understand that while quantum security is gaining traction, it might not fully replace traditional encryption methods in every scenario. Some cryptographic algorithms remain computationally secure even against quantum-based attacks, and not all data requires the level of protection offered by quantum-resistant encryption.
The editorial team of the Toptal Engineering Blog extends its thanks to Aditya Krishnakumar for reviewing the technical aspects of this article.