After two decades in cybersecurity, working with both large corporations and emerging startups, Ilia Tivin, a cybersecurity advisor at Toptal, possesses a comprehensive understanding of the field’s trajectory. This Q&A session summarizes a recent “ask me anything” forum on Slack, where Tivin addressed questions about the role of artificial intelligence (AI) in cybersecurity, posed by fellow Toptal engineers and security experts globally.
Note from the Editor: For clarity and conciseness, some questions and answers have been modified.
AI in Cybersecurity: Present and Future Applications
Is AI a necessity for modern cybersecurity?
—K.S., Montreal, Canada
I believe AI will become indispensable in the future. While AI’s current ability to develop exploits is relatively limited, it’s expected to advance over time, necessitating a corresponding strengthening of our defenses.
Have you encountered any instances where AI was employed to detect security breaches?
—J.O., Fortaleza, Brazil
The answer hinges on your definition of a security breach. When appropriately programmed, AI can effectively identify vulnerabilities by scanning and analyzing code. AI can also be used to create highly convincing phishing emails tailored with specific details about your organization. While I haven’t personally come across AI-driven security breaches beyond phishing, it doesn’t rule out their existence.
What are the potential drawbacks of using AI in cybersecurity?
—K.B., Bergerac, France
The disadvantages of AI in cybersecurity mirror those in other domains. By implementing AI, we entrust a level of decision-making to machines. However, comprehending how these machines reach their decisions isn’t always straightforward. Erroneous AI decisions concerning security automations, checks, or compliance can have significant consequences, potentially leading to substantial regulatory penalties, security breaches, or the loss of valuable intellectual property.
What new cybersecurity threats might emerge with modern AI technologies like generative AI?
—R.L., Lake Oswego, United States
One potential risk is an overdependence on AI, even with the latest advancements. As developers increasingly utilize AI for both coding and code review, there’s a possibility of inadvertently introducing security flaws into the codebase.
How could AI potentially enhance cybersecurity in the years to come?
—N.H., Tuzla, Bosnia and Herzegovina
Firstly, it’s hoped that AI will eliminate the provision of inaccurate information and errors. I anticipate a global shift toward increased automation. Furthermore, I foresee advancements in inspection techniques, although this progress might vary depending on the specific regulations and legal frameworks of the countries where AI companies operate. For instance, implementing enhanced inspection methods might be less likely in Europe due to its robust regulatory environment.
Implementing AI in Cybersecurity
Upsides | Downsides |
|---|---|
|
|
Real-world Examples of AI in Cybersecurity
Do you personally use any AI-powered cybersecurity tools, and if so, are there any you would recommend?
—M.D., Seattle, United States
In addition to the security provided by standard client security solutions, I utilize the AironWorks phishing simulation platform, which generates tailored phishing simulations to assess the preparedness and security awareness of employees within organizations. However, in terms of testing, I believe AI’s current capabilities in cybersecurity are somewhat limited. Although major companies tout the integration of AI into their cybersecurity products, the actual usability and effectiveness can vary significantly.
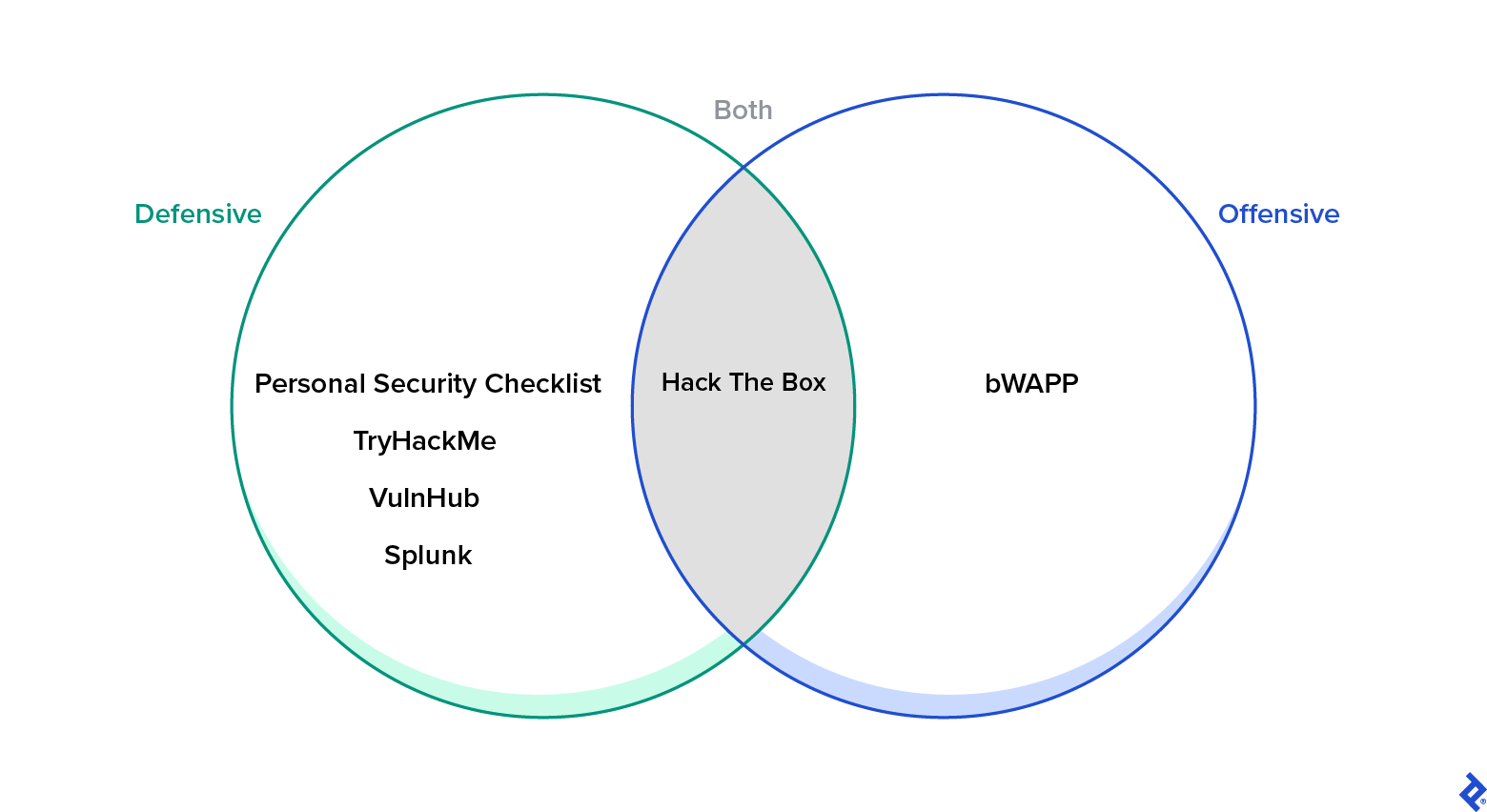
Are there any engaging websites where security enthusiasts can explore various aspects of offensive and defensive security?
—J.O., Fortaleza, Brazil
Personally, I’m a strong advocate for personal security. For those interested in the defensive side, I always recommend the Personal Security Checklist, a comprehensive GitHub repository containing over 300 tips and best practices for enhancing digital security and privacy. TryHackMe serves as an excellent starting point for delving into the world of security and even offers opportunities to participate in online challenges. While not frequently updated, VulnHub remains a valuable resource. The challenges offered by Splunk, though seemingly due for an update, are also worth exploring.
From an offensive security standpoint, bWAPP is a useful Docker container that provides a safe environment to practice exploiting web applications. Another noteworthy platform is Hack The Box, which offers a blend of both defensive and offensive security resources.
There seem to be differing opinions on Mac security. Some believe Macs are inherently secure, while others argue that caution is still necessary. What’s your perspective on this?
—M.Z., Santa Clarita, United States
The significantly smaller user base of Mac compared to PC might explain why cyberattacks predominantly target PCs. However, Mac users generally spend considerably more on their devices than PC users, making them an attractive target for financially motivated attacks. The recent surge in OS security patches released by Apple, coupled with a report published by Wired highlighting the article on this topic, suggests that Apple acknowledges the growing threat to Mac users.
Would you advise bolstering Mac security with antivirus software like Avast, or is it an unnecessary expense?
—M.Z., Santa Clarita, United States
Opting for the free ClamAV, coupled with diligently keeping your software up to date, is a viable strategy. Additionally, Microsoft Defender is now available for Mac users.
The editorial staff at the Toptal Engineering Blog expresses gratitude to Marco Jardim for reviewing the technical accuracy of the information presented in this article.