Safeguarding your business from the escalating dangers of ransomware has become a crucial aspect of strategic planning. Ransomware attacks are increasing, and in some cases, they are completely unavoidable. Ransomware groups have recently set their sights on large corporations, businesses, and even government entities. This guide will teach you how to shield your business from the growing menace of ransomware with essential steps and tips designed to safeguard all data against attacks.
This blog post focuses on practical advice and strategies you should integrate into your security measures and remain aware of.
What is ransomware?
For those unfamiliar with the term ‘ransomware,’ it refers to harmful software that targets your most valuable assets. This malware is engineered to encrypt your files, effectively locking you out of your system unless a ransom is paid.
Ransomware is meticulously crafted using powerful encryption algorithms that are incredibly difficult to crack. To regain access to your data, you’ll need a decryption key from the attackers themselves. Therefore, it’s always prudent to plan and employ the best techniques to ensure the security of your business.
Essential considerations for mitigating ransomware risks
While a strong security posture is crucial for addressing cyber threats, certain precautions are universally relevant for businesses of all types: This guide outlines protective measures against the growing threat of ransomware, offering key steps and tips to safeguard your data from attacks.
Backups are crucial: Protecting your business against ransomware threats
Data backups are non-negotiable. They maintain business continuity in case of unforeseen circumstances. Storing data in both cloud and offline storage is essential. However, remember that cloud storage can also be compromised. Therefore, adhering to the 3-2-1 backup strategy for critical data is highly recommended. This represents a sound approach to bolstering security against ransomware.
Prioritize update and patch management
Keeping your software, operating systems, and applications current is vital. Outdated applications or devices serve no purpose and Regular patches, making you an easier target for ransomware.
Implement network segmentation
Separating critical network operations from general ones is essential. By creating segments, you isolate sensitive systems and mitigate the impact of potential attacks.
Utilize email and web filtering
Employees can unwittingly download malicious files through untrusted links, potentially leading to ransomware attacks. To combat this, implement multi-login or two-factor authentication, and deploy email and web filters that block malicious attachments, phishing emails, and suspicious websites.
Prioritize training and employee education: Safeguarding your business from ransomware threats
Cyber risks continue to escalate daily. Educating your workforce about the dangers of ransomware is paramount. Train them to identify suspicious emails, calls, and other activities. Emphasize the significance of strong passwords, encryption protocols, and responsible privacy management.
Employ firewalls and intrusion detection systems
Activating firewalls and intrusion detection systems (IDS) helps monitor network traffic and identify unauthorized access attempts. This serves as a robust method for bolstering your defenses against ransomware threats.
Embrace endpoint security
Utilizing reputable antivirus and anti-malware software on your systems is crucial in mitigating ransomware risks. Regularly scanning your systems helps detect malware in real time, ensuring ongoing protection.
Create an incident response plan: Protecting your business against ransomware threats
Collaborate with your cybersecurity experts to develop a comprehensive incident response plan. This plan should outline steps to isolate infected devices or networks and detail the recovery process.
Explore cyber insurance
Consider obtaining cyber insurance to provide financial protection in the event of a ransomware attack. Insurance professionals can guide you on available options and coverage.
Recent ransomware attacks
According to the Unit 42 Incident Response team, 50% of ransomware attacks stem from a common vulnerability: attack surface exposure. This highlights the importance of implementing security measures to protect against ransomware.
Ransomware has transcended its initial objective of simply encrypting files and demanding Bitcoin. The emergence of new forms of harassment and multi-faceted extortion tactics renders traditional recommendations like backups alone insufficient.
For example, the Unit 42 Incident Response team team observed
- data theft in approximately 70% of ransomware cases involving negotiations (a significant increase from around 40% in mid-2021).
Let’s delve into some recent ransomware attacks to understand security tactics, steps, and tips for prevention and protection.
Clop ransomware gang: Protecting your business
The Clop ransomware group has been exploiting the MOVEit vulnerability to breach an expanding number of organizations, including several US federal agencies. Since Wednesday, June 13, this cybercriminal group has been steadily revealing the names of affected entities.
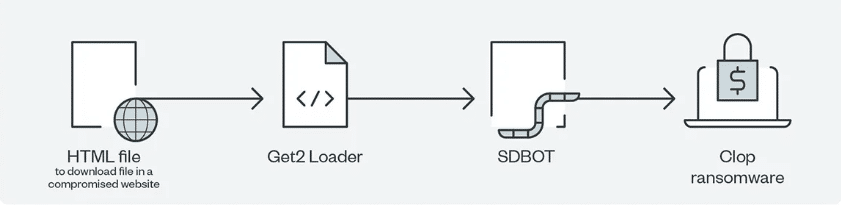
As of this publication, Clop has disclosed a total of 64 organizations on their data leak site, impacting almost every major industry. An increasing number of victims have confirmed these breaches.
Wednesday, June 14, marked the deadline set by Clop for victims of the large-scale breach of Progress Software’s MOVEit Transfer tool. The attackers threatened to publicly expose those who didn’t comply or engage in negotiations on their blog.
Big Head ransomware
A new ransomware strain called Big Head is spreading through a malvertising campaign disguised as fake Microsoft Windows updates and Word installers.
Fortinet FortiGuard Labs identified several versions of Big Head ransomware last month, all designed to encrypt files on victims’ computers and demand cryptocurrency payments in exchange for decryption.
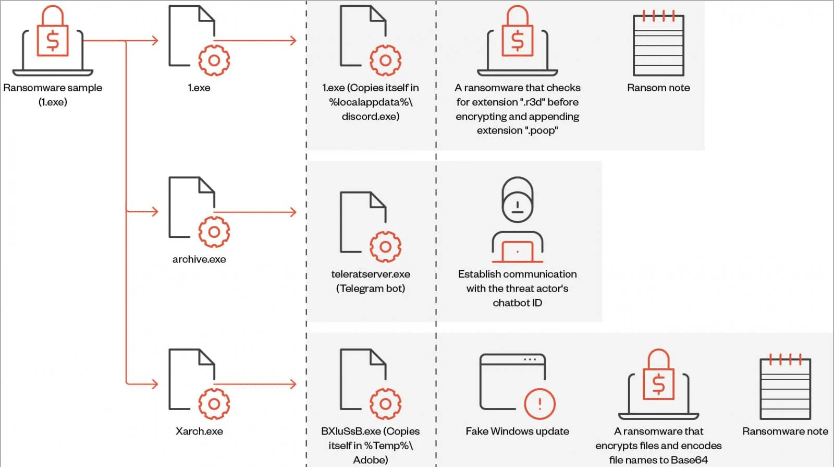
Source: TrendMicro
According to Fortinet researchers, one variant mimics a Windows Update, suggesting potential distribution through fake updates. Another variant uses a Microsoft Word icon, indicating likely distribution as counterfeit software.
The majority of identified Big Head ransomware samples originated from the United States, Spain, France, and Turkey.
In a recent analysis, Trend Micro provided insights into its functioning on Big Head, highlighting its capability to deploy three encrypted executable files. These insights provide valuable security tactics, steps, and tips to prevent and protect against this ransomware.
BlackByte 2.0 ransomware
A recent investigation by Microsoft’s Incident Response team unveiled the relentless and destructive nature of BlackByte 2.0 ransomware attacks, emphasizing their alarming speed.
Findings revealed that attackers can execute the entire attack process incredibly quickly, from gaining initial access to inflicting severe damage within just five days. They waste no time infiltrating systems, encrypting critical data, and extorting victims for its release.
This compressed timeframe poses a significant challenge for organizations striving to protect themselves against these malicious operations.
BlackByte ransomware takes center stage in the attack’s final phase, utilizing an 8-digit numerical key for data encryption.
To carry out these attacks, hackers employ a potent combination of tools and techniques. The investigation revealed the exploitation of unpatched Microsoft Exchange Servers as a highly successful tactic. By capitalizing on this vulnerability, they gain initial access to targeted networks, paving the way for their malicious activities.
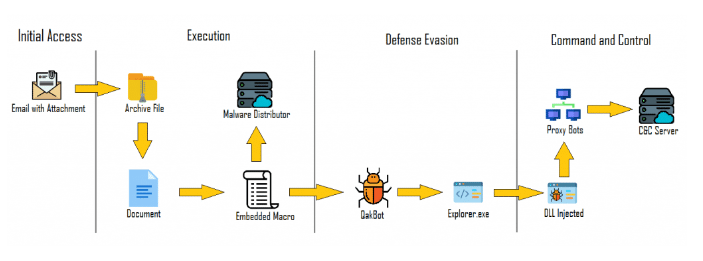
QBot malware campaign: Protecting your business from ransomware threats
Recent findings from Kaspersky have revealed a new QBot malware campaign that uses compromised business communications to trick individuals into installing the malware.
This latest wave, starting on April 4, 2023, has primarily targeted several countries, including Germany, Argentina, Italy, Algeria, Spain, the United States, Russia, France, the United Kingdom, and Morocco. The campaign aims to exploit vulnerabilities and emphasize the importance of steps and tips to prevent ransomware infections.
Source: CyberReasons
QBot, also known as Qakbot or Pinkslipbot, is a banking trojan active since at least 2007. Besides stealing passwords and cookies from web browsers, it acts as a backdoor for deploying additional malicious payloads like Cobalt Strike or ransomware.
Distributed through phishing campaigns, QBot has undergone continuous updates, incorporating anti-VM, anti-debugging, and anti-sandbox techniques to evade detection. In fact, Check Point. reported QBot as the most prevalent malware in March 2023.
MSI targeted by ransomware: Protecting your business
Taiwanese PC manufacturer Micro-Star International (MSI) officially confirmed that its systems were compromised in a cyberattack.
Upon detecting unusual network activities, MSI took immediate action, initiating incident response and recovery procedures. They also promptly notified law enforcement agencies.
However, MSI hasn’t disclosed specifics about the attack’s timing or whether sensitive data, such as source code, was compromised during the breach.
BlackCat malvertising
Cybercriminals behind the BlackCat ransomware have been observed using malvertising techniques to spread deceptive installers of the WinSCP file transfer application.
According to a recent analysis by Trend Micro researchers, malicious actors utilized malvertising by creating fake web pages mimicking legitimate organizations. In this instance, they impersonated the popular WinSCP application, an open-source Windows tool for file transfer.
Malvertising involves search engine optimization (SEO) poisoning, spreading techniques to propagate malware through online advertisements. Attackers hijack specific keywords like “WinSCP Download” and display fraudulent ads on search engine results pages of platforms like Bing and Google, redirecting unsuspecting users to malicious websites.
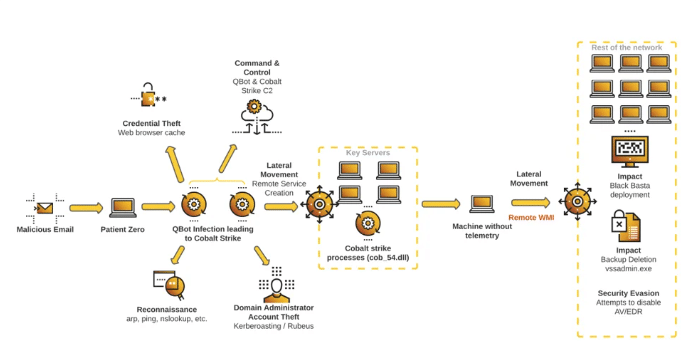
Qakbot ransomware: Protecting your business
A recent Qakbot malware campaign targeted American companies, leading to the infiltration of compromised networks with Black Basta ransomware infections.
Source: Securelist
According to a report by Cybereason researchers Joakim Kandefelt and Danielle Frankel, the Black Basta ransomware gang used QakBot malware in their latest campaign to gain an initial foothold and subsequently expand their presence within targeted organizations’ networks.
Ransomware’s rise as a significant threat
The constantly evolving tactics of cybercriminals mean you can never let your guard down. The exploitation of sophisticated malware campaigns like Black Basta and Clop highlights the critical importance of maintaining robust security measures. The repercussions of ransomware attacks can be devastating and have long-lasting consequences for businesses.
Vigilance, the adoption of strong cybersecurity practices, and a thorough understanding of the real-world problems posed by ransomware are essential. Now is the time to prioritize resilience in the face of this ever-present threat.
