Scala has become increasingly popular in recent years due to its seamless blend of functional and object-oriented programming paradigms, and its execution on the reliable Java Virtual Machine (JVM).
Despite compiling to Java bytecode, Scala is crafted to address several limitations perceived in Java. Offering comprehensive functional programming support, Scala’s syntax incorporates many implicit constructs that Java developers must build manually, often with significant complexity.
Developing a language that compiles to Java bytecode necessitates a profound understanding of the JVM’s internal mechanisms. To grasp the achievements of Scala’s creators, it’s crucial to delve deeper and examine how the compiler translates Scala source code into efficient JVM bytecode.
Let’s explore how these aspects are implemented.
Prerequisites
This article assumes a fundamental understanding of Java Virtual Machine bytecode. The complete virtual machine specification is available from Oracle’s official documentation. However, reading the entire specification isn’t essential for comprehending this article. I’ve provided a concise guide at the end for a quick introduction.
You’ll need a tool to disassemble Java bytecode to replicate the provided examples and conduct further investigation. The Java Development Kit includes a command-line utility called javap, which we’ll utilize here. A brief demonstration of javap is included in the guide at the end.
Naturally, readers who wish to follow along with the examples will require a functional installation of the Scala compiler. This article was written using Scala 2.11.7. Different Scala versions might generate slightly different bytecode.
Default Getters and Setters
While Java conventions dictate providing getter and setter methods for public attributes, Java programmers must write them explicitly, even though the pattern has remained unchanged for decades. In contrast, Scala offers default getters and setters.
Consider the following example:
| |
Let’s examine the Person class. Compiling this file with scalac and then executing $ javap -p Person.class yields:
| |
As evident, for every field in the Scala class, a corresponding field and getter method are generated. The field is private and final, while the method is public.
If we modify the Person source code by replacing val with var and recompile, the field’s final modifier is removed, and the setter method is also included:
| |
When a val or var is defined within the class body, the corresponding private field and accessor methods are created and initialized accordingly during instance creation.
It’s worth noting that this implementation of class-level val and var fields implies that if any variables are used at the class level to store temporary values and are never accessed directly by the programmer, initializing each such field will add one or two methods to the class footprint. Adding a private modifier to such fields doesn’t eliminate the corresponding accessors; it merely makes them private.
Variable and Function Definitions
Suppose we have a method called m() and create three different Scala-style references to this function:
| |
How are these references to m constructed? When is m executed in each case? Let’s analyze the resulting bytecode. The following output displays the results of javap -v Person.class (excluding extraneous output):
| |
The constant pool reveals that the reference to method m() is stored at index #30. Examining the constructor code, we observe that this method is invoked twice during initialization, with the instruction invokevirtual #30 appearing initially at byte offset 11 and then at offset 19. The first invocation is followed by the instruction putfield #22, which assigns the method’s result to the field m1, referenced by index #22 in the constant pool. The second invocation follows the same pattern, assigning the value to the field m2, indexed at #24 in the constant pool.
In essence, assigning a method to a variable declared with val or var only assigns the result of the method to that variable. We can see that the generated methods m1() and m2() are simply getters for these variables. In the case of var m2, we also observe the creation of the setter m2_$eq(int), which behaves like any other setter, overwriting the field’s value.
However, employing the keyword def produces a different outcome. Instead of retrieving a field value to return, the method m3() also includes the instruction invokevirtual #30. This means that whenever this method is called, it subsequently calls m() and returns the result of that method.
Therefore, Scala offers three ways to work with class fields, easily specified using the keywords val, var, and def. In Java, we would need to implement the necessary setters and getters explicitly, resulting in less expressive and more error-prone boilerplate code.
Lazy Values
The generated code becomes more intricate when declaring a lazy value. Let’s assume we add the following field to the previously defined class:
| |
Running javap -p -v Person.class now reveals the following:
| |
In this scenario, the value of the field m4 is not computed until required. The compiler generates a special private method called m4$lzycompute() to calculate the lazy value and the field bitmap$0 to monitor its state. The method m4() checks if the field’s value is 0, signifying that m4 has not been initialized. If so, it invokes m4$lzycompute(), populates m4, and returns its value. This private method also sets the value of bitmap$0 to 1, ensuring that the next time m4() is called, it bypasses the initialization method and directly returns the value of m4.

Scala generates bytecode that is both thread-safe and efficient. To achieve thread safety, the lazy compute method utilizes the monitorenter/monitorexit instruction pair. Efficiency is maintained because the synchronization overhead only occurs during the first read of the lazy value.
A single bit is sufficient to indicate the state of the lazy value. Consequently, a single int field can track up to 32 lazy values. If the source code defines more than one lazy value, the compiler modifies the bytecode to implement a bitmask for this purpose.
Once again, Scala allows us to leverage a specific behavior that would require explicit implementation in Java, saving effort and minimizing the potential for errors.
Function as Value
Let’s now examine the following Scala source code:
| |
The Printer class has a field named output with the type String => Unit, representing a function that takes a String and returns an object of type Unit (similar to void in Java). In the main method, we create an instance of this object and assign an anonymous function to the field that prints a given string.
Compiling this code generates four class files:
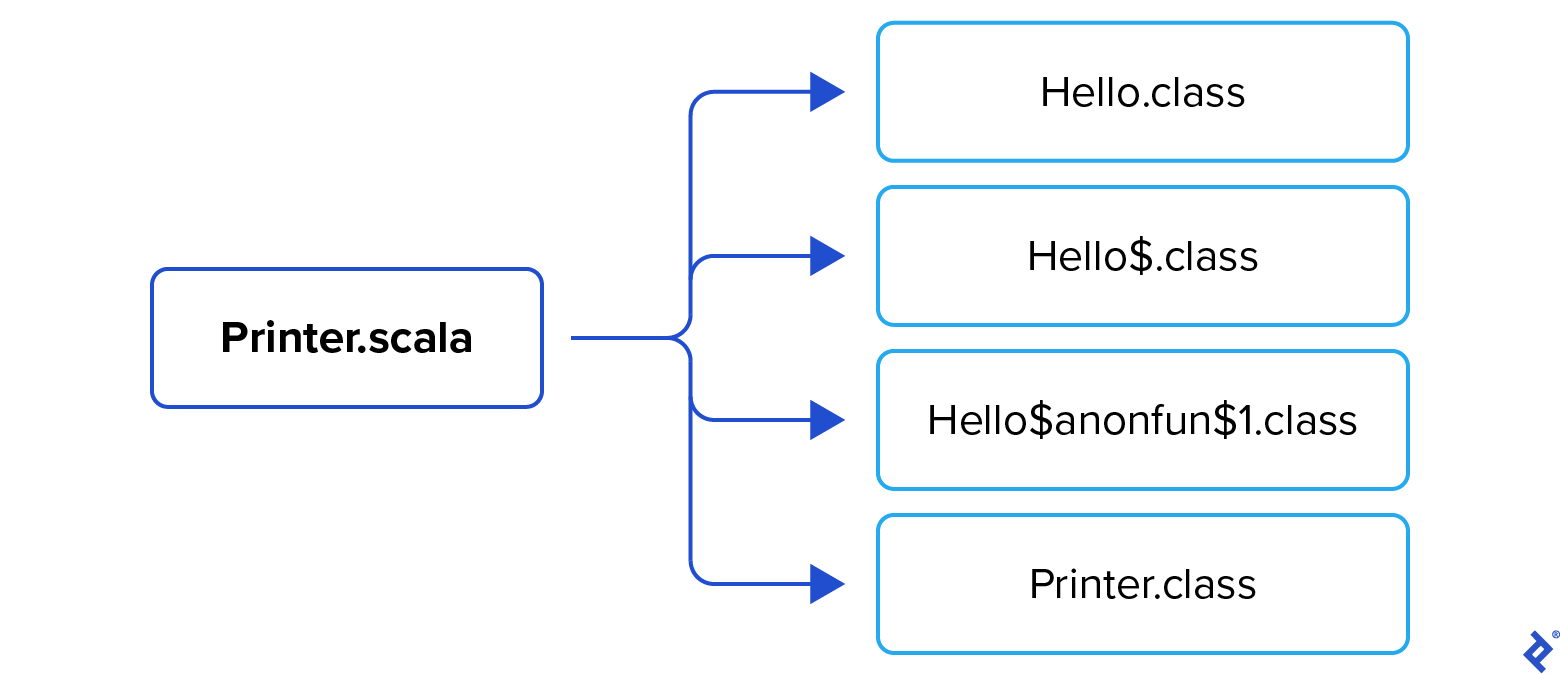
Hello.class acts as a wrapper class whose main method simply invokes Hello$.main():
| |
The hidden Hello$.class houses the actual implementation of the main method. To examine its bytecode, ensure you properly escape the $ character according to your command shell’s rules to prevent its interpretation as a special character:
| |
The method instantiates a Printer object and creates a Hello$$anonfun$1 object containing our anonymous function s => println(s). The Printer is initialized with this object as the value for the output field. This field is then loaded onto the stack and executed with the operand "Hello".
Next, let’s analyze the anonymous function class, Hello$$anonfun$1.class. We can observe that it extends Scala’s Function1 (as AbstractFunction1) by implementing the apply() method. It actually creates two apply() methods, one wrapping the other, responsible for type checking (in this case, ensuring the input is a String) and executing the anonymous function (printing the input using println()).
| |
Referring back to the Hello$.main() method above, we see that at offset 21, the anonymous function is invoked by calling its apply( Object ) method.
Lastly, for completeness, let’s examine the bytecode for Printer.class:
| |
The anonymous function is treated like any other val variable, stored in the class field output, and the getter method output() is generated. The only distinction is that this variable must now implement the Scala interface scala.Function1 (which AbstractFunction1 does).
Therefore, the cost of this elegant Scala feature is the underlying utility classes created to represent and execute a single anonymous function that can be used as a value. You should consider the number of such functions and your VM implementation’s details to determine the implications for your application.
Scala Traits
Scala traits resemble interfaces in Java. The following trait defines two method signatures and provides a default implementation for the second one. Let’s see how it’s implemented:
| |
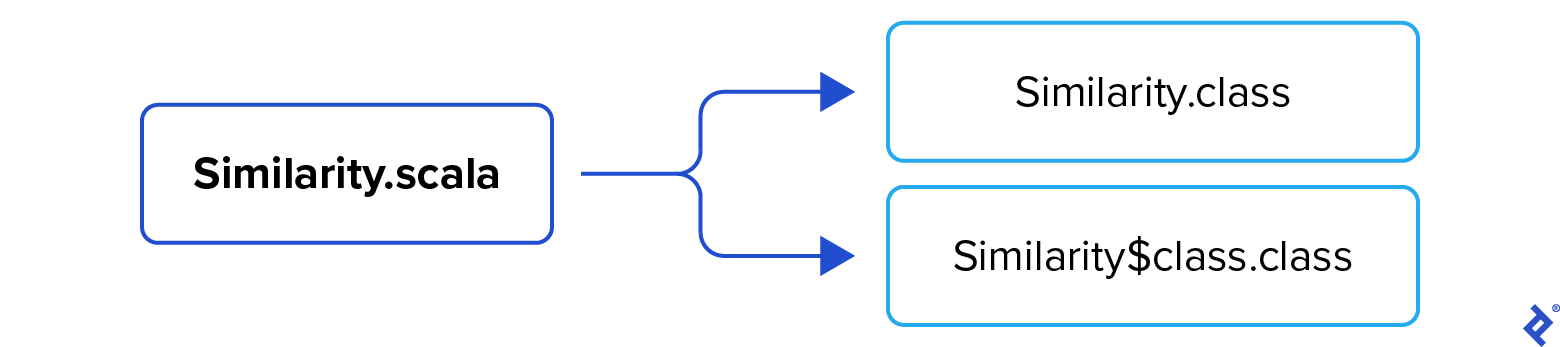
Two entities are generated: Similarity.class, the interface declaring both methods, and the synthetic class Similarity$class.class, which provides the default implementation:
| |
| |
When a class implements this trait and calls the isNotSimilar method, the Scala compiler generates the bytecode instruction invokestatic to call the static method provided by the accompanying class.
Traits can be combined to create intricate polymorphism and inheritance structures. For instance, multiple traits and the implementing class can all override a method with the same signature, using super.methodName() to delegate control to the next trait. When the Scala compiler encounters such calls:
- It identifies the specific trait assumed by the call.
- It determines the name of the accompanying class that provides the static method bytecode defined for the trait.
- It generates the necessary
invokestaticinstruction.
Hence, the powerful concept of traits is implemented at the JVM level without incurring significant overhead, allowing Scala programmers to utilize this feature without concerns about runtime performance.
Singletons
Scala allows the explicit definition of singleton classes using the object keyword. Consider the following singleton class:
| |
The compiler produces two class files:
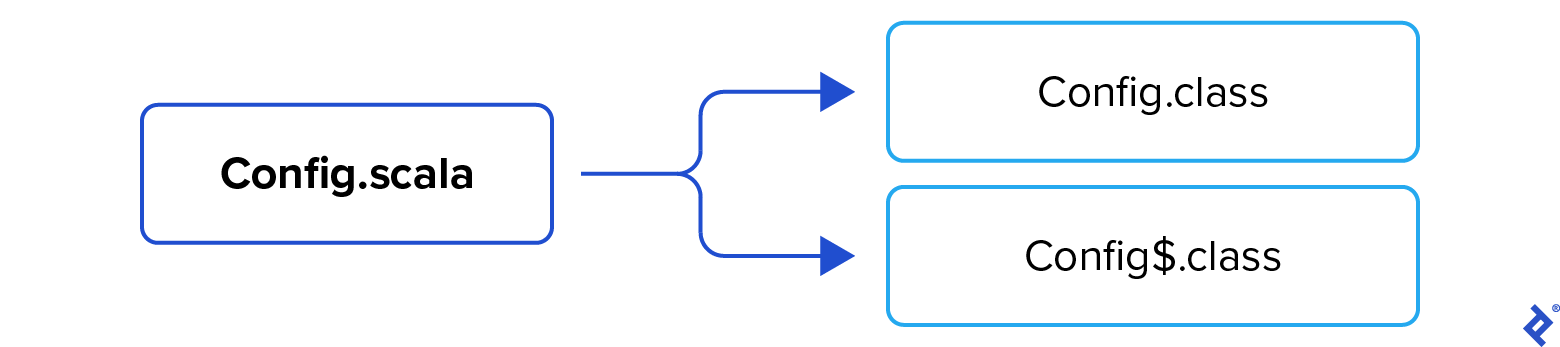
Config.class is relatively straightforward:
| |
It serves as a decorator for the synthetic Config$ class, which encapsulates the singleton’s functionality. Examining this class with javap -p -c reveals the following bytecode:
| |
It consists of the following:
- The synthetic variable
MODULE$, providing access to the singleton object. - The static initializer
{}(also known as<clinit>, the class initializer) and the private methodConfig$, responsible for initializingMODULE$and setting its fields to default values. - A getter method for the static field
home_dir. In this case, there’s only one method. If the singleton has more fields, it will have additional getters and setters for mutable fields.
The singleton pattern is a widely used and valuable design pattern. While Java doesn’t offer a direct language-level mechanism for specifying singletons, Scala provides a clear and convenient way to declare them explicitly using the object keyword. As we’ve observed, its implementation is both efficient and straightforward.
Conclusion
We’ve explored how Scala compiles several implicit and functional programming features into sophisticated Java bytecode structures. This glimpse into Scala’s inner workings provides a deeper appreciation for its capabilities, enabling us to maximize its potential.
Moreover, we now possess the tools to investigate the language independently. Numerous other useful features of Scala’s syntax, such as case classes, currying, and list comprehensions, are beyond the scope of this article. I encourage you to delve into Scala’s implementation of these constructs and become a true Scala ninja!
The Java Virtual Machine: A Crash Course
Similar to the Java compiler, the Scala compiler transforms source code into .class files containing Java bytecode for execution by the Java Virtual Machine. To comprehend the differences between the two languages under the hood, it’s essential to understand their target system. This section provides a concise overview of crucial elements in the Java Virtual Machine architecture, class file structure, and assembler fundamentals.
This guide only covers the minimum necessary to follow the article’s content. While many significant JVM components are omitted here, comprehensive information is available in the official documentation: here.
Decompiling Class Files with
javapConstant Pool Field and Method Tables JVM Bytecode Method Calls and the Call Stack Execution on the Operand Stack Local Variables Return to Top
Decompiling Class Files with javap
Java includes the command-line utility javap, which decompiles .class files into a human-readable format. Since both Scala and Java class files target the same JVM, javap can be used to inspect class files compiled from Scala code.
Let’s compile the following source code:
| |
Compiling with scalac RegularPolygon.scala generates RegularPolygon.class. Executing javap RegularPolygon.class displays the following output:
| |
This is a basic breakdown of the class file, showing the names and types of the class’s public members. Adding the -p option includes private members:
| |
This still doesn’t provide much information. To examine the implementation of methods in Java bytecode, let’s use the -c option:
| |
This is more interesting, but to get the complete picture, we’ll use the -v or -verbose option, as in javap -p -v RegularPolygon.class:
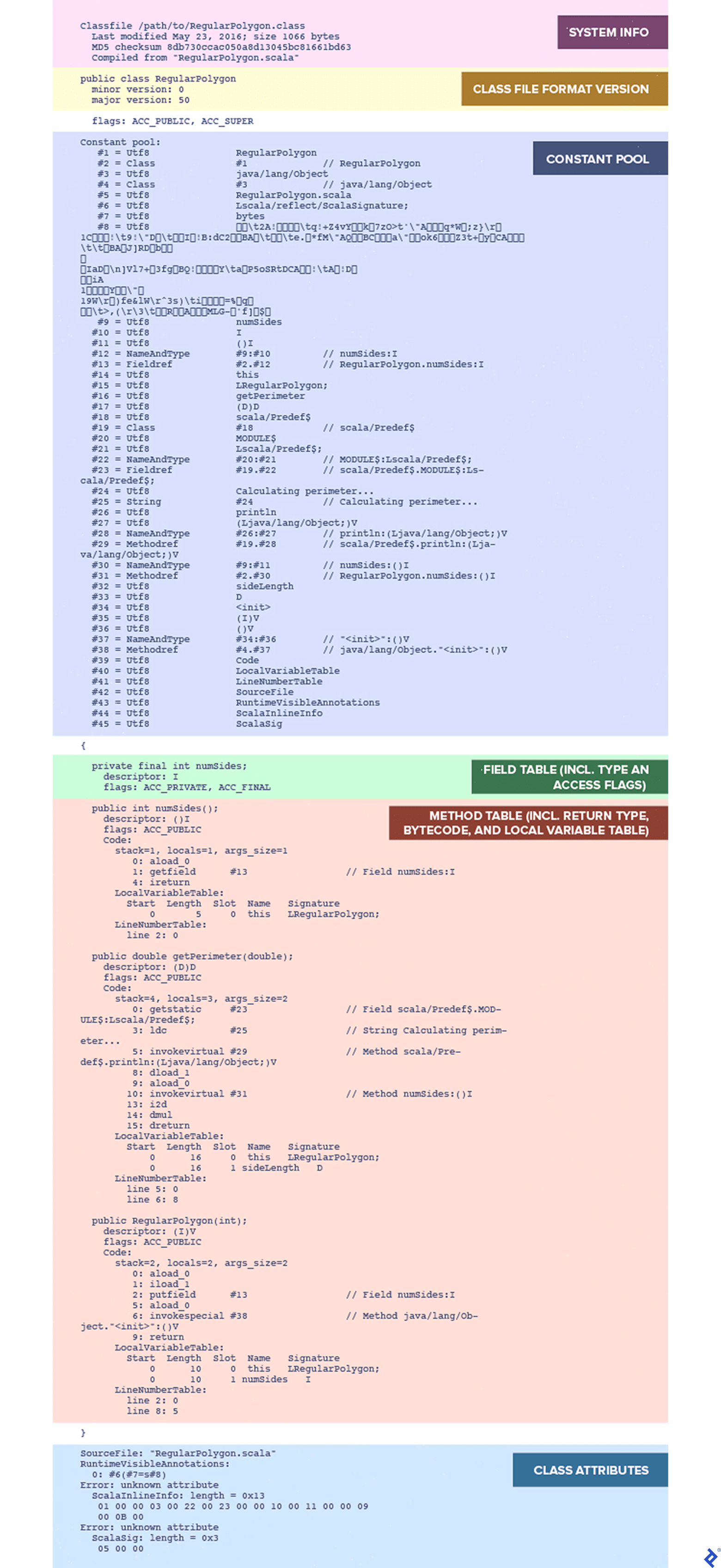
Now we see the class file’s contents. Let’s break down some crucial parts.
Constant Pool
The C++ development cycle involves compilation and linking stages. However, Java skips an explicit linking stage because linking occurs at runtime. The class file must support this runtime linking, meaning that when source code references any field or method, the resulting bytecode must retain relevant references in symbolic form. These symbolic references are resolved by the runtime linker once the application loads into memory and actual addresses become available. This symbolic form must contain:
- class name
- field or method name
- type information
The class file format specification includes a section called the constant pool, a table of all references required by the linker. It consists of entries with various types.
| |
The first byte of each entry is a numeric tag identifying the entry type. The remaining bytes provide information about the entry’s value, with the number of bytes and interpretation rules depending on the type indicated by the first byte.
For instance, a Java class using the constant integer 365 might have a constant pool entry with the following bytecode:
| |
The first byte, x03, identifies the entry type as CONSTANT_Integer, informing the linker that the next four bytes represent the integer’s value. (Note that 365 in hexadecimal is x16D.) If this is the 14th entry in the constant pool, javap -v displays it as:
| |
Many constant types are composed of references to more “primitive” constant types elsewhere in the constant pool. For example, our sample code includes the statement:
| |
Using a string constant results in two constant pool entries: one with type CONSTANT_String and another with type CONSTANT_Utf8. The Constant_UTF8 entry contains the actual UTF8 representation of the string value, while the CONSTANT_String entry references the CONSTANT_Utf8 entry:
| |
This complexity arises because other constant pool entry types reference Utf8 entries but are not String entries themselves. For instance, any reference to a class attribute generates a CONSTANT_Fieldref entry, which contains references to the class name, attribute name, and attribute type:
| |
For a more detailed explanation of the constant pool, refer to the JVM documentation.
Field and Method Tables
Each class file contains a field table with information about every field (attribute) defined in the class. These are references to constant pool entries describing the field’s name, type, access control flags, and other relevant data.
A similar method table is also present in the class file. However, besides name and type information, it contains the actual bytecode instructions executed by the JVM for each non-abstract method, along with data structures used by the method’s stack frame (described later).
JVM Bytecode
The JVM employs its internal instruction set to execute compiled code. Running javap with the -c option displays the compiled method implementations. Inspecting our RegularPolygon.class file this way, we see the following output for the getPerimeter() method:
| |
The actual bytecode might resemble:
| |
Each instruction begins with a one-byte opcode identifying the JVM instruction, followed by zero or more instruction operands depending on the specific instruction’s format. These operands are typically constant values or references to the constant pool. javap helpfully translates the bytecode into a human-readable form, displaying:
- The offset, representing the instruction’s first byte’s position within the code.
- The human-readable name or mnemonic of the instruction.
- The operand’s value, if any.
Operands displayed with a pound sign, such as #23, are references to constant pool entries. As shown, javap also generates helpful comments identifying the referenced pool entry.
We’ll discuss some common instructions below. For comprehensive information about the complete JVM instruction set, refer to the documentation.
Method Calls and the Call Stack
Each method call requires its own execution context, including locally declared variables and arguments passed to the method. Together, these constitute a stack frame. Upon method invocation, a new frame is created and placed on top of the call stack. When the method returns, the current frame is removed and discarded, restoring the frame that was active before the method call.
A stack frame comprises several distinct structures. Two crucial ones are the operand stack and the local variable table, discussed next.
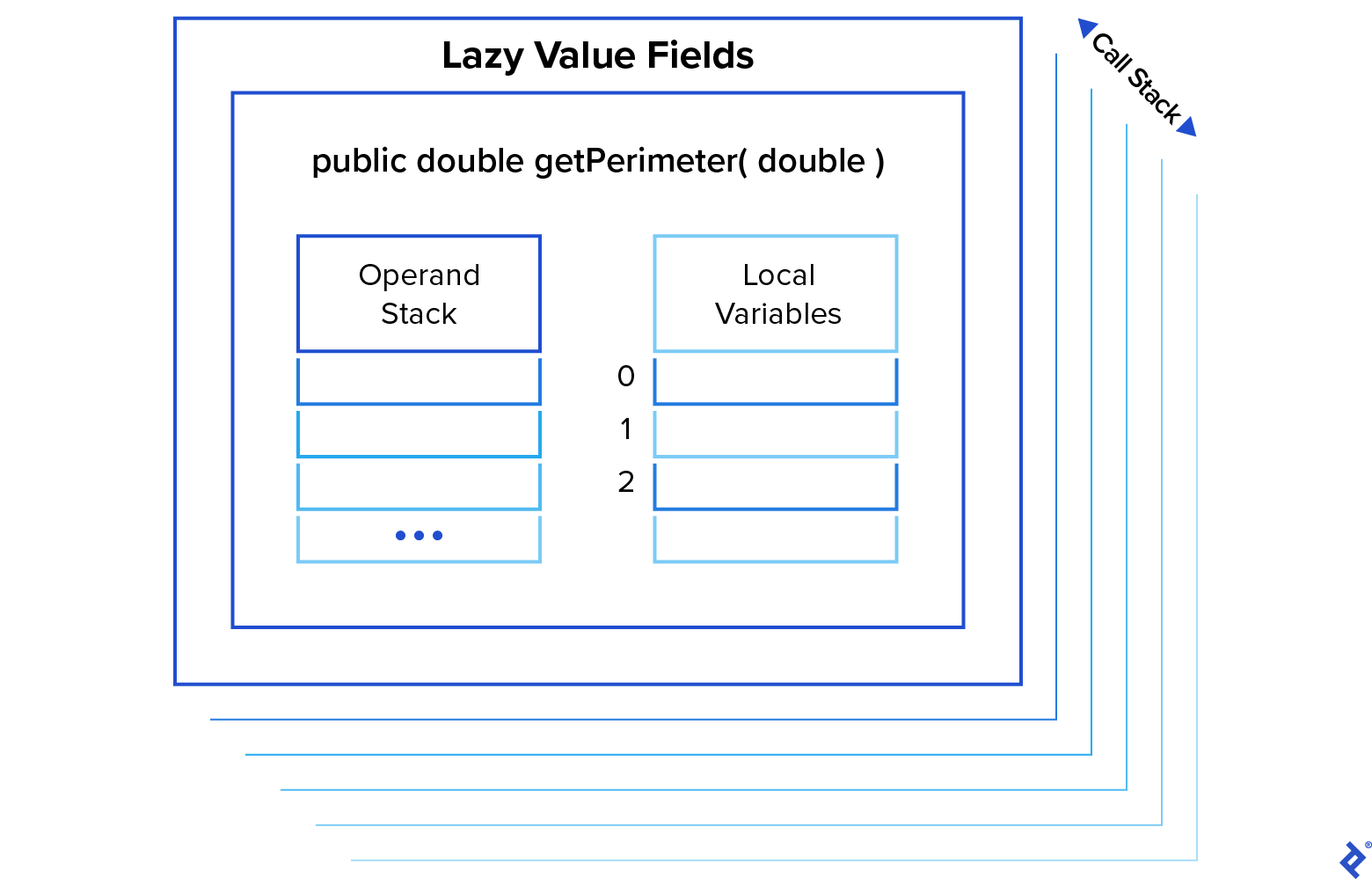
Execution on the Operand Stack
Many JVM instructions operate on their frame’s operand stack. Instead of explicitly specifying a constant operand in the bytecode, these instructions take values from the operand stack’s top as input, typically removing these values during the process. Some instructions also push new values onto the stack. This way, JVM instructions can be combined to perform complex operations. For example, the expression:
| |
compiles to the following in our getPerimeter() method:
| |
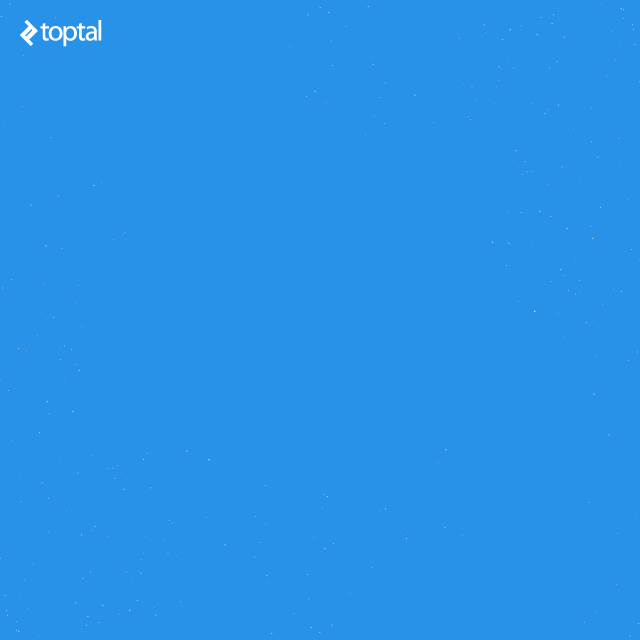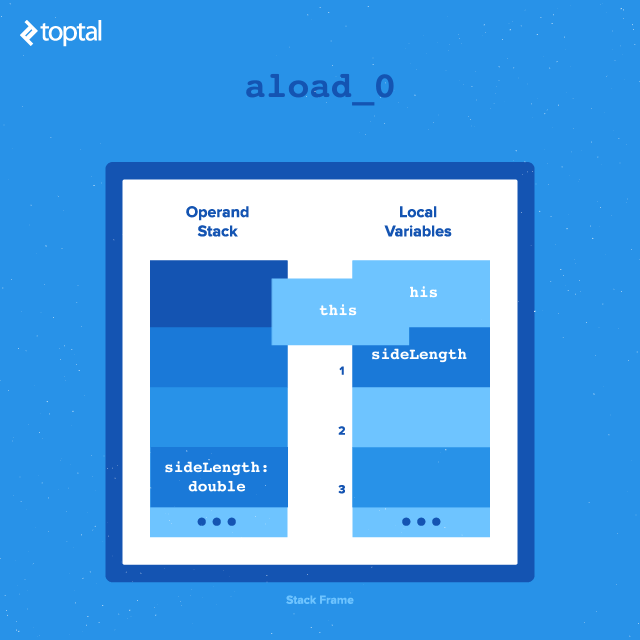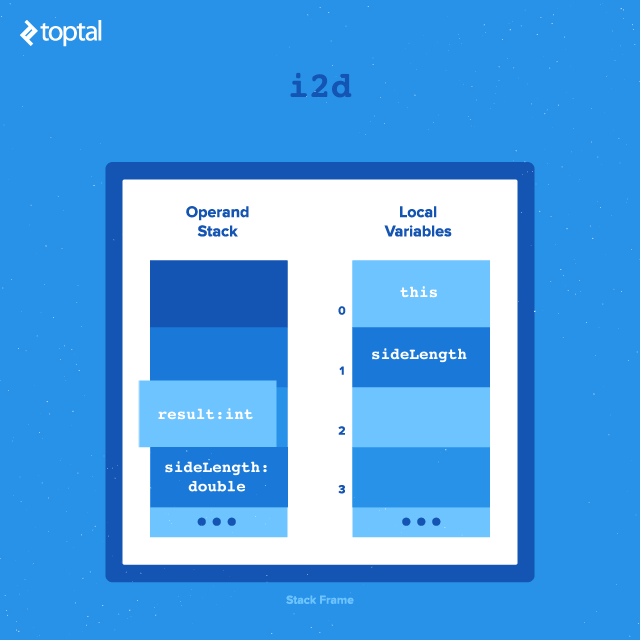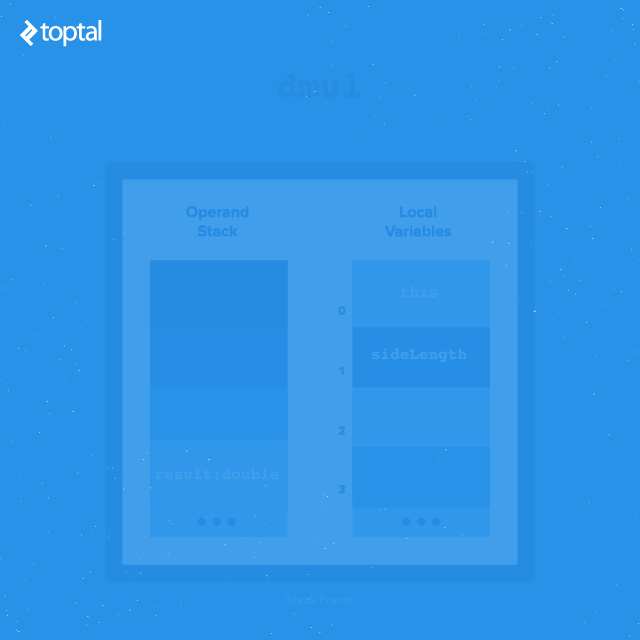
- The first instruction,
dload_1, pushes the object reference from slot 1 of the local variable table (discussed next) onto the operand stack. In this case, it’s the method argumentsideLength. - Next,
aload_0pushes the object reference at slot 0 of the local variable table onto the operand stack. This is almost always the reference tothis, the current class. - This sets up the stack for the subsequent call,
invokevirtual #31, which executes the instance methodnumSides().invokevirtualpops the top operand (the reference tothis) to determine the class from which to call the method. Upon method return, its result is pushed onto the stack. - Here, the returned value (
numSides) is an integer. It needs conversion to a double floating-point format for multiplication with another double value. The instructioni2dpops the integer value, converts it to floating-point format, and pushes it back onto the stack. - At this point, the stack contains the floating-point result of
this.numSideson top, followed by the value of thesideLengthargument passed to the method.dmulpops these two values, performs floating-point multiplication, and pushes the result onto the stack.
When a method is called, a new operand stack is created as part of its stack frame, where operations are performed. It’s important to distinguish between the terms “stack,” which can refer to the call stack (the stack of frames providing context for method execution) or a specific frame’s operand stack (where JVM instructions operate).
Local Variables
Each stack frame maintains a table of local variables, typically including a reference to the this object, arguments passed during the method call, and any local variables declared within the method body. Running javap with the -v option displays information about setting up each method’s stack frame, including its local variable table:
| |
In this example, there are two local variables. The variable in slot 0 is named this and has the type RegularPolygon, representing the reference to the method’s own class. The variable in slot 1 is named sideLength and has the type D (indicating a double), representing the argument passed to our getPerimeter() method.
Instructions such as iload_1, fstore_2, or aload [n] transfer different types of local variables between the operand stack and the local variable table. Since the first item in the table is usually the reference to this, the instruction aload_0 is common in methods operating on their own class.
This concludes our brief exploration of JVM basics.